Feature flags, also known as feature toggles, are powerful tools used in software development to enable or disable functionality within a software application. They allow for safe deployments and testing in production, help to enable continuous delivery, and permit experimentation with new features. However, managing feature flags can be complex, requiring careful planning, coordination, and monitoring.
One effective method for managing feature flags is to categorize them based on their longevity and purpose. There are several types of flags such as release flags, which are short-lived and used to facilitate trunk-based development, and experiment flags, used for A/B testing. Understanding the type of flag and its purpose can aid in deciding when to retire it, thus preventing flag debt.
Another approach is to use a feature flag management system. These systems provide a centralized location to manage flags and can offer additional functionality like flag status reporting, user segmentation, and integration with other tools. They also help in avoiding common issues like flag conflicts and flag sprawl.
Additionally, it’s crucial to implement a process for retiring flags once they are no longer needed. Not doing so can lead to technical debt. A common practice is to tie the lifecycle of a feature flag to the feature it’s toggling. Once the feature is fully operational and stable, the flag should be retired.
Furthermore, setting naming conventions for feature flags can improve manageability. A well-named feature flag is easier to understand and track. The name should be reflective of the feature it is toggling and include an indicator of its intended use.
It is also recommended to monitor the usage of feature flags closely. Monitoring helps to identify any potential issues early, such as flags that are not behaving as expected or are causing performance issues. Using a feature flag management system can facilitate this process, as it can provide comprehensive data on flag usage.
Lastly, it is essential to communicate clearly about feature flags across the team. Everyone involved should understand why a flag is being introduced, what its intended use is, and when it should be retired. This can prevent misunderstandings and mistakes, ensuring that the use of feature flags contributes positively to the development process.
In conclusion, managing feature flags effectively requires a combination of strategic planning, careful monitoring, and clear communication. By adopting these practices, teams can harness the power of feature flags to accelerate software delivery while minimizing risks.
Understanding Feature Flags
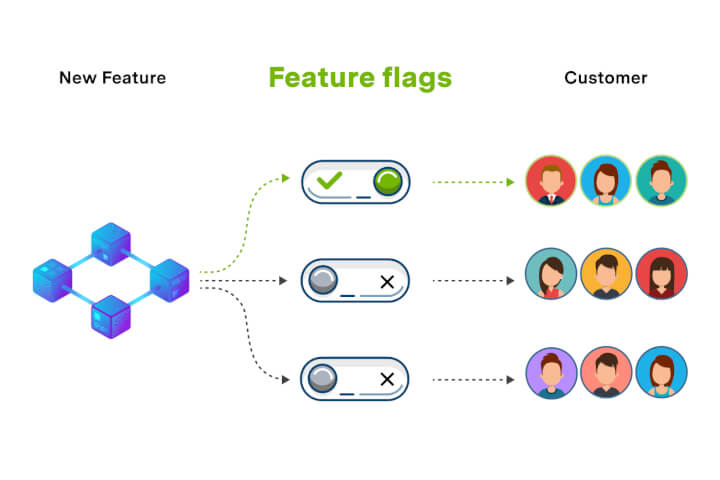
Feature flags, also known as feature toggles, are a powerful tool in the field of software development that allow developers to switch on or off certain parts of an application or system without having to deploy new code. This method provides a great deal of flexibility, as it enables the testing of new features in a live environment without impacting the end-user experience.
This feature management technique is widely used in Continuous Integration and Continuous Deployment (CI/CD) practices. The core idea behind feature flags is to separate feature rollout from code deployment, thereby reducing risk and increasing control over features. By using feature flags, developers can mitigate the impact of failed deployments, as they can simply turn off the feature if it’s not working as expected.
Furthermore, it allows for A/B testing, canary releases, and phased rollouts, which are beneficial in assessing user engagement and feedback. However, it’s essential to manage and clean up old flags to avoid technical debt. In essence, understanding feature flags is crucial for anyone involved in software development, as they provide a safer, more controlled environment for releasing new features.
Steps to Implement Feature Flags
Implementing feature flags involves several critical steps. First, define the feature flag, which represents a new functionality you want to test or gradually roll out. Then, decide on the type of flag you need. There are mainly two types — ‘release flags’ for entire features and ‘experimental flags’ for testing variations of features. After deciding, you need to code the flag into the application. This involves creating conditional statements in the code that will determine whether the new feature will be active or inactive.
Next, configure the feature flag in the flag management system. This system helps manage the lifecycle of all feature flags, including the ability to turn them on or off and define who can access them. Once configured, you can deploy the code. This step involves releasing the feature flagged code into the production environment. However, this doesn’t mean the new feature is live. Since it’s behind a flag, you can control when and to whom it will be available.
The following step is to perform testing. This stage is critical as it helps ensure the new feature works as expected and doesn’t cause any breaking changes to the existing system. Testing can be done in a controlled environment, and any necessary adjustments can be made before releasing the feature to a larger audience.
The penultimate step is the rollout. Based on testing results and business needs, you can gradually roll out the feature to a subset of users, monitor their feedback, and adjust accordingly. Finally, once you’re satisfied with the feature’s performance, you can perform a full rollout, making the feature available to all users. Remember to clean up the code by removing the feature flag once it’s no longer needed. This is done to avoid technical debt and keep the codebase clean and manageable. These are the fundamental steps to implement feature flags.
Developing an Access Control System
Developing an effective access control system is a critical component in the arena of information security and asset protection. The essence of an access control system is to regulate who or what can view or utilize resources in a computing environment. It is a fundamental concept in security that reduces risk to the system. An efficient system consists of two main components: authentication and authorization. Authentication verifies the identity of the user by validating their credentials, while authorization involves granting or denying access to specific resources based on the user’s authenticated identity.
Designing such a system necessitates careful consideration of several factors. Firstly, it is essential to identify the appropriate access control model based on organizational goals, risk tolerance, and overall security strategy. The three most common models include discretionary access control, mandatory access control, and role-based access control. Each model varies in terms of complexity and security level, hence the selection should align with the unique needs of the organization.
Furthermore, password management and user access auditing are integral elements of an access control system. Password management involves establishing password complexity requirements and reset policies, whereas user access auditing entails monitoring and logging all attempts to access system resources. This ensures that any potential breaches can be swiftly detected and mitigated.
Lastly, continuous monitoring and updating of the access control system is crucial to adapt to evolving security risks and techniques. It is imperative to conduct regular assessments and audits to identify any potential vulnerabilities and promptly implement necessary modifications. By doing so, the system remains robust and resilient against potential security threats. Hence, developing an efficient access control system is an ongoing process that requires strategic planning, consistent monitoring, and proactive management.
Strategies for Safely Deactivating Feature Flags
Feature flags, also known as feature toggles, are a critical tool in continuous development, allowing developers to release a version of a product that has hidden features. These can be toggled on or off without deploying new code. This provides a way to separate feature rollout from code deployment, and offers a safety net when introducing new features. However, deactivating feature flags needs to be done carefully to avoid potential risks or system failures.
One of the strategies for safely deactivating feature flags is to use a phased approach. This means gradually disabling the feature flag for small groups of users, and then progressively increasing the size of the group. By monitoring the system’s behavior during each phase, developers can identify and resolve any unexpected problems before they affect a larger population of users.
Another effective method is to use a kill switch. A kill switch allows developers to quickly disable a feature if it is causing issues, without having to roll back the entire deployment. This provides an immediate solution while the problem is being investigated and resolved.
Regularly auditing feature flags is also an important strategy. This involves checking which flags are still active and if they are still necessary. Old or unnecessary feature flags can cause code clutter and confusion, and can increase the risk of errors. By regularly reviewing and cleaning up feature flags, developers can maintain a clean, manageable codebase.
Overall, it is essential to have a clear strategy for managing and deactivating feature flags. This should include clear processes for when and how flags are introduced, how they are monitored, and how and when they are deactivated. By following these strategies, developers can use feature flags to improve their development process, while minimizing the potential risks.
Integrating Feature Flags into Development Processes
Integrating feature flags into development processes is an increasingly popular practice in software development that offers several benefits. Feature flags, also known as toggles or switches, allow developers to hide, enable, or disable certain features in a software product without having to change the code. This is especially helpful in continuous integration and continuous delivery (CI/CD) environments, where code is frequently merged and deployed.
The utilization of feature flags allows for safer deployments and aids in mitigating risk. If a particular feature is causing issues in production, it can be turned off immediately without needing to roll back the entire deployment. This not only saves time but also reduces potential impact on the user experience. Furthermore, it offers the ability to test new features in the live environment with a select group of users. This can provide valuable feedback and data before a full-scale rollout.
Moreover, feature flags can foster a more effective collaboration between developers, QA testers, and product managers. They can control the visibility and rollout of features, and can troubleshoot and fix issues more efficiently. Additionally, they offer a way to experiment and innovate without disrupting the main user base, which can lead to the development of more robust and user-friendly software solutions.
However, while integrating feature flags into development processes can offer many advantages, it needs to be done carefully and strategically. Poorly managed feature flags can lead to code complexity, technical debt, and can even create new bugs if not handled properly. Therefore, it’s essential to have a system in place for managing and cleaning up old flags to avoid clutter and confusion.
In conclusion, feature flags can be a powerful tool in the software development process when used correctly. They offer a way to release and test new features safely, reduce risk, and foster innovation. But, like any tool, they need to be managed properly to reap their full benefits.
